How Hackers Are Going For Gold At Rio’s Olympics
This month’s Olympic Games in Rio de Janeiro aren’t just a showcase of the greatest athletes from around the globe: They’re already a target for the world’s online criminals, experts warn.
Rio’s police are on alert against crime and terrorism, with an impressive surveillance system and warnings to Olympic visitors to stay alert. Cybersecurity experts say visitors must be careful about their digital safety and data too.
“The Olympics attracts a lot of people,” says Thomas Fischer, principal threat researcher at security firm Digital Guardian. “That’s a prime target for attackers to look at as far as, ‘how can we get them to give us some money?'”
And, he says, the risk isn’t limited to the 500,000 expected visitors traveling to Rio for the Games, which run through Aug. 21. Hackers are also likely to target the multinational companies that partner with the IOC, including the Coca-Cola Co., General Electric, McDonald’s Corp, Visa, Samsung Electronics, and Bridgestone, and will even find ways to target those watching from home.
Phishing In An Olympic-Sized Pool
Olympics fans will be seen as a lucrative target for email phishing attacks, just because there are so many of them, warns Fischer. One avenue will be scammers selling counterfeit tickets to those planning to attend the Games—something security firm Kaspersky reported finding online this spring.
“On phishing websites users have been asked to provide personal information—including bank account details—to pay for the fake Olympic Games tickets,” the company warned. “After extracting this information, criminals use it to steal money from victim bank accounts. To sound even more convincing, fraudsters are informing their victims that they will receive their tickets two or three weeks before the actual event.”
In a report published last week, the U.S. cybersecurity research firm Fortinet warned of a recent surge of suspicious websites in Brazil. “The volume of malicious and phishing artifacts (i.e., domain names and URLs) in Brazil is on the rise,” the company wrote. “The highest percentage growth was in the malicious URL category, at 83 percent, compared to 16 percent for the rest of the world.”
Fraudulent emails and social media posts will also likely offer links to video clips, downloadable apps, games, and other content that can distribute malware to those watching from home, security experts say. That’s happened at past major sporting events, like when phishing attacks targeted soccer fans around the 2014 World Cup. Security experts also reported similar phishing attempts revolving around that year’s Winter Olympics in Sochi, Russia.
“All of these are looking at scamming you in some way to get personal data or to get access to your machine,” Fischer says. “Ransomware is the big thing right now—I think we’ll see a lot of phishing scams that will either direct you to downloading a piece of malware or running a piece of malware out of the email.”
Email scammers may also invite fans to gamble on the Games, with criminals themselves betting that those trying to place illegal wagers will be less likely to call police if something goes wrong, says Samir Kapuria, senior vice president of Cyber Security Services at Symantec.
Some security software, including Kaspersky’s, has already begun to filter out bogus domain names with strings like “rio2016” in them, and even users not using such software can take basic precautions, like questioning any offers that just seem too enticing.
“The first thing is to just be aware that these things exist,” says Kapuria. “If something looks too good to be true, it likely is too good to be true.”
Bank card readers and ATMs are yet another vulnerability, IT security firm Trend Micro has warned. In one scheme, chip-and-PIN machines—long used in Europe and often considered secure—can skim information from chips and the four-digit PINs that cardholders enter. In another scheme, a card fitted with a doctored chip can insert malware into legitimate card readers, which transmits future card information and personal data to thieves, who can quickly clone the cards. Another common scheme in Brazil involves so-called Chupa Cabras, plastic skimmers inserted into the card slots of ATMs.
Last year, 49% of Brazilians reported experiencing some kind of credit card fraud—an annual jump of 19%. Only Mexico beat Brazil, with a card fraud rate of 56%, according to a survey by ACI Worldwide and the Aite Group; the U.S. is in third place with 47%.
Last week, a reporter for a North Carolina newspaper reported that his card was hacked immediately after using it at the gift shop at the IOC press center. And on Friday, two McClatchy reporters in Rio said their cards had been hacked and cloned soon after arrival.
Visitors also shouldn’t accept any kind of promotional USB sticks distributed by advertisers, since they can also carry malware, warns security company Tripwire. “Putting an unknown USB stick into your device is simply asking for trouble,” says a statement from the company.
Watching Out For Counterfeit Hotspots
Fans attending the Games will inevitably want to share selfies or just get some work done while in Rio, meaning they’ll be searching for Wi-Fi hotspots to let them get online. Criminals are likely respond to that impulse by setting up rogue Wi-Fi access points that surreptitiously log activity and data, including unencrypted usernames and passwords, or even inject malware into web traffic, warns Fischer.
“[They’ll] be able to capture all the traffic and read it as it’s going through or analyze later to extract usernames and passwords,” he says.
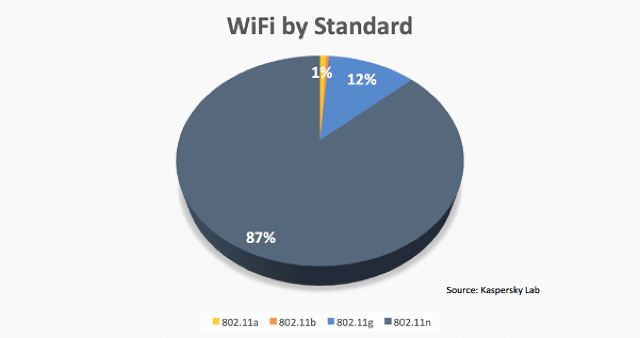
In an analysis last month of over 4,500 unique wireless access points around Rio, Kaspersky found that about a quarter of them are vulnerable or insecure, protected with an obsolete encryption algorithm or with no encryption at all.
During last month’s Republican National Convention in Cleveland, security firm Avast Software tested attendees’ awareness about Wi-Fi security by setting up access points with a mix of pro-Republican network names and others mimicking brands like Starbucks and AT&T. More than 1,200 people connected to the networks, which could have put them at risk had the hotspots been set up by someone malicious, the company said.
Olympic officials might be able to detect and shut down any rogue access points that pop up at event sites themselves, but it would be considerably more challenging for them to do so everywhere tourists would gather, says Fischer. “The problem lies with when it’s actually going to outside the event perimeter.”
Those who do use open wireless access points can help keep themselves safe by using virtual private networks, which will encrypt traffic even before it passes over the air to reach the access point, says Kapuria.
“If you’re using an open Wi-Fi, a VPN is the right way to encrypt your traffic and make sure that’s secure,” he says.
Stockholm-based wireless technology provider Aptilo Networks has said that it’s working with telecom companies to provide wireless connections at Olympic venues, transportation hubs, beaches, and cafes in the Rio area. The company has said that it’s taking steps to ensure security and suitable bandwidth for those visiting for the Games, though it wasn’t able to make someone available for an interview to discuss those steps in detail. Brazilian telecom company Linktel has said it’s working with Aptilo and with international Wi-Fi carriers like Boingo and AT&T to let their subscribers connect to its network with their own credentials.
Messing With The Games Themselves
It’s also possible that activist hackers or other digital miscreants will try to tamper with the infrastructure surrounding the Games themselves.
“The biggest [attack] they’ll have is potentially someone trying to do a denial of service,” says Fischer. That is, someone may attempt to disrupt the networks officials use to communicate scores and other data in an effort to disrupt the tight event schedule, he says. One possible attack would be to jam official wireless networks, or to inject data packets that force the networks to repeatedly disconnect, making it hard for data to get through.
Denial-of-service attacks often rely on botnets, servers that have been commandeered by hackers to overwhelm computers with data requests. According to Symantec’s 2016 Internet Security Report, “Brazil was one of the top 10 countries for Botnet attacks.”
“If you do a denial of service, you’re going to disrupt the games, and that’s going to look bad, and have more impact that anything else,” says Fischer.
Ideally, organizers will be able to log those types of attacks, and use signal detection hardware to find where the rogue broadcasts are coming from, he says.
In a statement to Bloomberg, Atos SE, the France-based information technology partner of the International Olympics Committee (IOC), said that cybersecurity is a “priority” and that it “has implemented the latest cybersecurity technologies to protect the games IT infrastructure and systems.”
Fast Company , Read Full Story
(54)