Apple just turned iCloud into a digital Fort Knox
Last week, I wrote an article calling out Apple’s Messages for its backup’s lack of end-to-end encryption on iCloud. Because the iCloud backups of a user’s Apple Messages were merely encrypted and not end-to-end encrypted, I advised individuals—such as activists and journalists—who wanted the most privacy and security for their text messages to ditch Apple Messages for Meta’s WhatsApp, which does end-to-end encrypt message backups.
Today, my article is already outdated. That’s because Apple has announced its most significant privacy enhancements in years. The major one is called Advanced Data Protection, and it effectively lets users choose to turn their iCloud account into a digital Fort Knox by letting them store nearly all their iCloud data in an end-to-end encrypted state on Apple’s servers. That means that Apple itself cannot access the user’s data—even if given a valid court order from a less-than-democratic nation-state. It also means that, should Apple’s iCloud servers ever be hacked, the hacker would still not be able to access the majority of a user’s iCloud data, provided they’ve enabled Advanced Data Protection.
Why online cloud end-to-end encryption is more important than ever
Apple gave me a sneak peek of Advanced Data Protection (January 01, 2023) and also explained the company’s rationale behind offering the improved privacy and security option to the company’s users.
Apple says that as the world has moved to online cloud solutions (think: iCloud, Google Docs, Dropbox), it’s been both a blessing and a curse. The blessing is you can sign into your online cloud account, like iCloud, from anywhere, and access all of your data from any device and keep all data synced between multiple devices. The convenience that this provides to our daily lives is obvious.
But Apple also noted that as the world has moved to the cloud, so have hackers and other bad actors. Back in the old pre-cloud era, a hacker would need access to a user’s physical device if they wanted to grab their data. But now that user data is on the cloud, hackers can just focus on accessing remote cloud servers—no physical access to an individual’s laptop or phone needed.
Apple cites research that shows the number of global data breaches more than tripled between 2013 and 2021. Even more alarming: More than 60% of America’s 1,000 largest companies have experienced a public data breach. And then, of course, there is also an uptick in nation-state attacks and threats from private organizations that sell hacking tools.
That reality represents a frightening prospect for journalists, activists, and, increasingly, women who use messaging apps to discuss their abortion options. However, it’s a prospect many in those groups—and others—previously just had to live with, because the majority of online cloud services don’t end-to-end encrypt all user data on the cloud. Much of the time that data is merely encrypted, with the cloud service provider holding a copy of the decryption key—a key that a hacker could get ahold of or a government could gain access to through a court order.
But with Advanced Data Protection, such scenarios are something iCloud users likely don’t have to worry much about anymore.
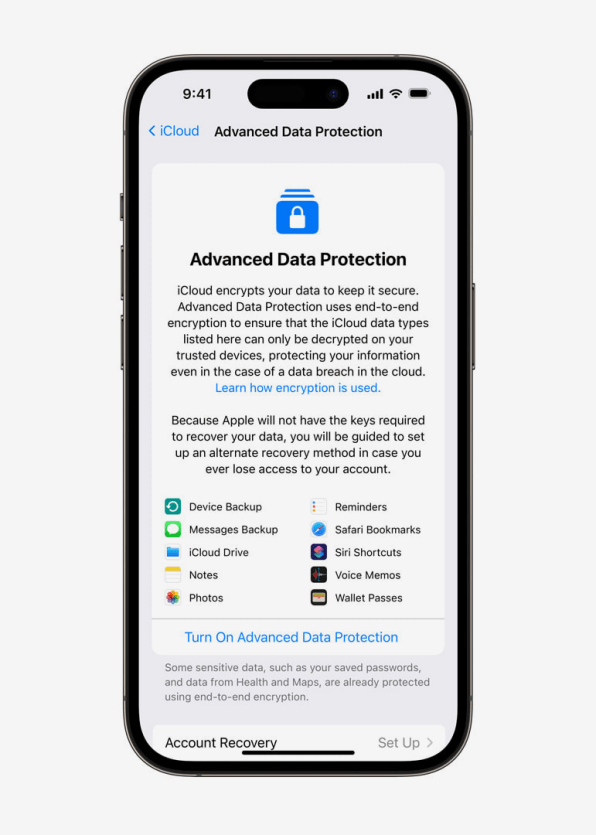
What iCloud user data does Advanced Data Protection end-to-end encrypt?
It should be noted that some iCloud user data has always been end-to-end encrypted on Apple’s servers. This means that even Apple itself could not access the data—even at the user’s request.
iCloud data that has been and remains end-to-end encrypted by default includes:
That’s not a bad list and shows that Apple has always end-to-end encrypted your most sensitive data, such as health data and passwords, on iCloud. But if a user chooses to enable Advanced Data Protection, additional iCloud data—data that could be significantly more revealing about the user—will now be end-to-end encrypted, too, including:
There are only three major types of iCloud data that will not be end-to-end encrypted, even with Advanced Data Protection turned on. These are iCloud Mail, iCloud Contacts, and iCloud Calendars. Apple says the reason for this is that Mail, Contacts, and Calendars rely on legacy internet technology that needs to remain compatible with third-party email services and third-party email clients. End-to-end-encrypting that data would likely break such compatibility.
iCloud’s Advanced Data Protection does come with risks
While iCloud’s new Advanced Data Protection is sure to please privacy advocates, it does come with some risk for the user. Because nearly all of a user’s iCloud data is end-to-end encrypted with Advanced Data Protection turned on, if users ever forget their passwords, their data is effectively gone.
That’s because when Advanced Data Protection is enabled, even Apple has no way of decrypting a user’s iCloud data, so it could not help the user restore theirs. It’s also why Apple has built-in two ways in which an iCloud user who gets locked out of their Advanced Data Protected iCloud account can be let back in. The first is by generating account recovery keys the user can print out and save when they enable Advanced Data Protection. Recovery keys are a standard feature of most services that uses end-to-end encryption.
A second way a user can get back into their Advanced Data Protected iCloud account if they lose their password is by setting up a recovery contact, which can be any other person with an Apple ID and Apple device. It should be noted that this recovery contact will never be able to access the user’s iCloud data—they’ll simply serve as a means for allowing that user to get back into their iCloud account.
More Apple privacy and security features coming soon
iCloud’s Advanced Data Protection rolls out to beta testers today, and Apple says the feature will go live to all users in the United States by the end of December (with other regions to follow next year).
But Advanced Data Protection isn’t the only new privacy and security feature that Apple has announced. The company says it will also launch iMessage Contact Key Verification next year. This will allow iMessage users to verify that the person they are texting is actually the person the account claims to be. Users will be able to verify codes with each other over the phone or in person.
Finally, Apple also says that early 2023 will see the rollout of support for physical security keys for Apple ID logins. Physical security keys are small devices a user must plug into their computer or phone when logging into an account (Apple is also supporting NFC-capable security keys). They’ve been in use for years and can be seen as an even more advanced form of standard two-factor authentication. Physical security keys aren’t something everyone will use—but activists, journalists, and government officials will probably want to do so.
After stumbling on the privacy front last year, Apple has now cranked its privacy initiatives to an 11, and today’s announcements show that Apple is still the Big Tech privacy king.
(35)