Hackers could use light to burglarize you through your security camera
Researchers at Israel’s Ben-Gurion University of the Negev have demonstrated in a new paper how hacked security cameras with night vision capabilities can be used to secretly transmit to and receive data even from networks that are not connected to the internet.
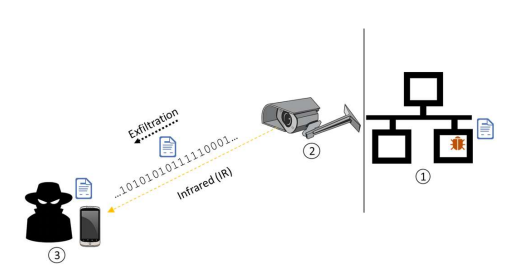
Night vision cameras use infrared (IR) light to see without illuminating the area in a way visible to humans. If they’re compromised, hackers can flash that infrared lamp on and off to transmit data to anyone in range without people being able to see that the camera is behaving strangely. The camera’s lens can also be used to pick up additional commands from attackers who aim infrared light signals at it.
Imagine that hackers are aiming to hack a network that isn’t even linked to the rest of the internet. If they can get malware onto a publicly viewable IR-equipped surveillance camera that’s connected to that network, attackers could then essentially use the camera as a kind of modem to connect to the network too: A keyhole through which the pre-installed malware could be controlled, or data could be manipulated or stolen.
“Security cameras are unique in that they have ‘one leg’ inside the organization, connected to the internal networks for security purposes, and ‘the other leg’ outside the organization, aimed specifically at a nearby public space, providing very convenient optical access from various directions and angles,” said Mordechai Guri, head of the research team, in a statement.
The researchers say the attackers can communicate with the cameras at a distance of tens to hundreds of meters away. “Data can be leaked from [a] network at a bit rate of 20 bit/sec (per camera) and be delivered to the network at bit rate of more than 100 bit/sec (per camera),” the researchers said.
Here’s a video in which researchers use a camera to steal data, passwords, and selected passages of The Adventures of Tom Sawyer:
(Here’s another video about using the cameras to communicate with the network.)
The same researchers at Ben-Gurion’s Cyber Security Research Center have previously shown how disk lights and hard drive noise can be used to steal data. One experiment even focused on using compromised internet-enabled air conditioners to adjust temperatures as a signal to malware on computers on a separate network. In a recent demonstration by a separate security group at the University of Washington, researchers showed how they could use a smart speaker and a pop song to “see” where you are in a room.
(29)

