Microsoft officially ended its support for most Windows XP computers back in 2014, but today it’s delivering one more public patch for the 16-year-old OS. As described in a post on its Windows Security blog, it’s taking this “highly unusual” step after customers worldwide including England’s National Health Service suffered a hit from “WannaCrypt” ransomware. Microsoft patched all of its currently supported systems to fix the flaw back in March, but now there’s an update available for unsupported systems too, including Windows XP, Windows 8 and Windows Server 2003, which you can grab here (note: if that link isn’t working then there are direct download links available in the Security blog post).
Of course, for home users, if you’re still running one of those old operating systems then yes, you should patch immediately — and follow up with an upgrade to something current. If you’re running a vulnerable system and can’t install the patch for some reason, Microsoft has two pieces of advice:
- Disable SMBv1 with the steps documented at Microsoft Knowledge Base Article 2696547 and as recommended previously.
- Consider adding a rule on your router or firewall to block incoming SMB traffic on port 445
Update: Microsoft legal chief Brad Smith has written a blog post that both calls for more help from customers (read: update more often) and chastises intelligence agencies for hoarding security exploits. They don’t understand the risk to the public if the exploits leak, Smith says — it’s as if someone stole a batch of Tomahawk missiles. We wouldn’t count on the NSA or other agencies heeding the call, but Microsoft clearly wants to make its frustrations heard.
An additional blog post explains Microsoft’s analysis of how the malware spreads. On newer versions like Windows Vista, 7, 8.1 and 10, the March update tagged MS17-010 addresses the vulnerability it’s exploiting (that was revealed earlier this year by “The Shadow Brokers” when they leaked a stolen cache of NSA tools). While it’s not confirmed how the initial infections occurred, it’s believed the trojan horse was spread by email phishing links that drop the “EternalBlue” exploit released by The Shadow Brokers, as well as the WannaCrypt malware variant. Interestingly, it doesn’t even try to attack Windows 10, focusing solely on Windows 7/8 and earlier operating systems that are still vulnerable to the attack.
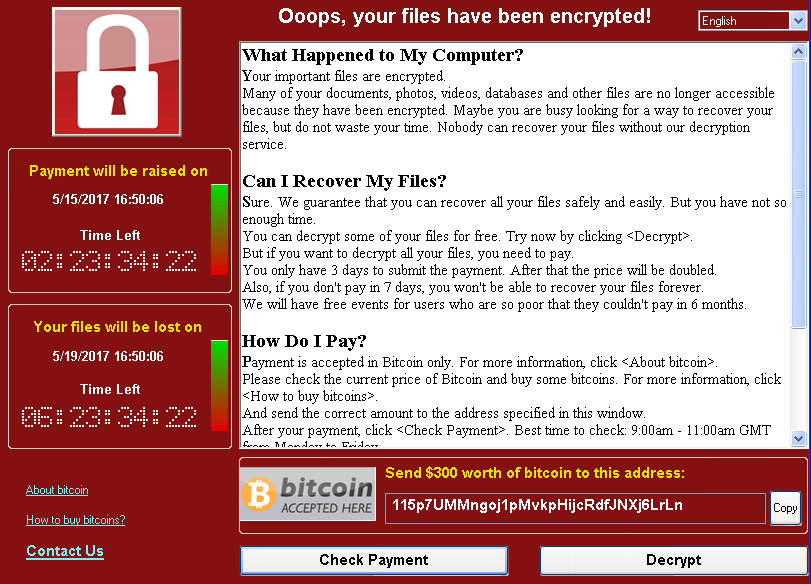
Once it’s on a computer, it goes on locking up the user’s files and arranging the ransom message. The spread of the initial release has actually stopped (after infecting more than 123,000 computers) because security researchers registered a domain that the malware checks before the infection starts. As long as the software finds it, a sort of killswitch engages and no encryption occurs. However, as @MalwareTechBlog notes, anyone could modify the attack to remove the killswitch and begin attacking computers again.
That’s because even without phishing links, another part of the exploit the searches out a vulnerable server component (SMBv1) on unpatched Windows machines and can infect them remotely. This probably won’t work across the internet for PCs behind a firewall or router, but if a server is connected directly to the internet, or a PC is on the same network as an infected computer, it can spread quickly — which is exactly what happened (May 27, 2017).
So I can only add”accidentally stopped an international cyber attack” to my Résumé. ^^
— MalwareTech (@MalwareTechBlog) May 13, 2017
(44)
