The Billion-Dollar Company Helping Governments Hack Our Phones
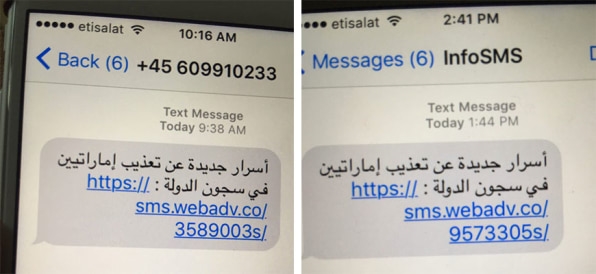
Last August, Ahmed Mansoor, a human-rights defender based in the United Arab Emirates, received a text message from an unknown phone number. The SMS promised “new secrets about the torture of Emiratis in state prisons,” and included a hyperlink to an unfamiliar website.
Mansoor wisely didn’t click the link. He took a screenshot of the message and sent it to an investigator at Citizen Lab, a digital rights group at the Munk School at the University of Toronto, which had helped identify previous hack attacks on Mansoor’s phone. With this link and his help, they would eventually uncover the work of a mysterious seven-year-old Israeli company, NSO Group, that has built its business on the back of one product: a spyware suite known as Pegasus.
“Anything you can do on the phone, Pegasus can do on your phone,” says John Scott-Railton, a senior researcher at Citizen Lab, which released its initial findings on the spyware in August 2016. “Turning on the camera and watching somebody in the room, turning on the microphone and listening to somebody: It can even do some things that you can’t, like put files on the phone and take files off, to manipulate data on the phone.”
By reading messages and listening to calls either before or after they are encrypted, Pegasus can foil encryption; by deleting itself, it can foil forensic researchers trying to understand it. Those who have analyzed it call it the most sophisticated commercial spyware yet to be made public.
[Photo: Citizen Lab]
Pegasus probably hasn’t been installed on your phone. NSO says it only sells to governments for legitimate reasons, like spying on criminals and terrorists, and that it complies with Israel’s export rules. The spyware’s not cheap either: According to a price list seen last year, NSO charges customers $650,000 to hack 10 devices, on top of a $500,000 installation fee.
But the growing and loosely regulated market for Pegasus and other cyberweapons also represents a serious risk, say security experts, an upgrade to the age-old dilemma surrounding any legitimate arms sales: what happens to a weapon after it’s been sold?
“What is concerning is that there is a gold rush right now to invest in companies doing offensive spyware stuff,” says Scott-Railton. “It’s happening without a lot of attention paid to the ethical and human-rights risks.”
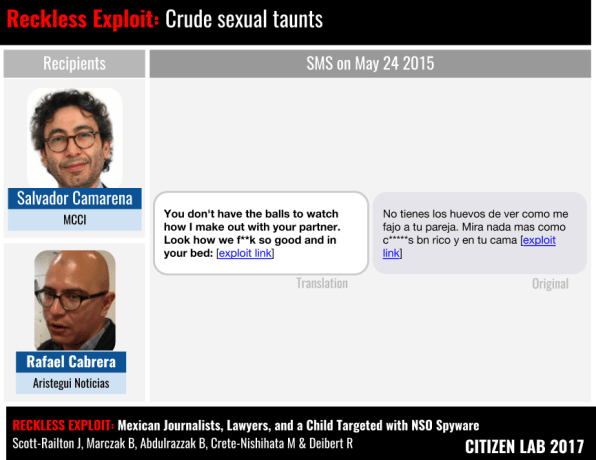
In June, Citizen Lab and the New York Times reported that Mexican government officials had used Pegasus to spy on the mobile devices of journalists, human-rights activists, lawyers, and others looking into murders, corruption, and the disappearance of dozens of college students. Pegasus had even been deployed against the phones of scientists and public health campaigners who supported measures to reduce childhood obesity, including Mexico’s “Soda Tax.” Since 2011, the Times reported, at least three Mexican government agencies paid NSO Group $80 million for the software.
In a statement, NSO said it only sells to “authorized” government customers and denied having any knowledge of the attacks in Mexico. President Enrique Peña Nieto called for an inquiry, even as he insisted that surveillance software had only been used in cases involving national security and organized crime. Lately, however, the investigation has been slowed by what forensic experts say is an unnecessary demand—that victims turn over their phones—and so far, no one has been charged with any wrongdoing.
“We Don’t Talk To Journalists”
Mexico and the UAE aren’t the only countries where commercially made, government-only cyberweapons have been aimed at activists and lawyers, and NSO isn’t the only company making this kind of software: Citizen Lab has also helped investigations into abuse of spyware made by the Italian company Hacking Team and the Munich-based Gamma Group.
“This is an industry where the narrative of companies that sell government-exclusive spyware is, ‘We sell this to support criminal investigations and track terrorists,’” says Scott-Railton. “But in practice, many governments lack the oversight that prevents them from using it in ways that are clearly abusive and have nothing to do with national security.”
NSO doesn’t disclose its clients, but according to Citizen Lab it has registered web domains, presumably for hacking purposes, in a number of countries with dubious civil rights records, including Uzbekistan, Bahrain, Kenya, Saudi Arabia, Nigeria, Turkey, Qatar, Yemen, Hungary. In 2013, NSO executives told the Financial Times they had visited about 35 countries over the previous 18 months. (In the UAE, Mansoor, the activist targeted by Pegasus, was detained by authorities in March on charges of “cybercrimes” and using social media to “publish false information that harm national unity and damage the country’s reputation.” Amnesty International said it feared he was being held in solitary confinement and was at risk of torture.)
 .
.
[Photo: Martin Ennals Foundation]
Like many of Israel’s cybersecurity startups, NSO was founded in 2010 by three veterans of the Israeli military’s signals interception group Unit 8200, Omri Lavie, Shalev Hulio, and Niv Carmi. Today, the company has over 200 employees at its headquarters in the coastal startup hub of Herzliya, according to its LinkedIn profile. A sales arm based in Bethesda, Maryland, WestBridge Technologies, sells “top-of-the-line technologies to various government agencies in North America, particularly in the U.S.,” its LinkedIn profile says.
Emails obtained by Motherboard show that at some point before January 2015, WestBridge met with U.S. Drug Enforcement Administration officials to pitch its software. There is no evidence however, of what, if any, deals NSO has entered into with U.S. agencies.
NSO did not respond to emailed questions from Fast Company, and Lavie, the company’s cofounder and U.S. representative, did not reply to questions sent to him via Twitter. A person who answered the phone at the Bethesda office was curt: “We don’t talk to journalists.”
NSO’s government ties have also made a cameo in ongoing inquiries into the Trump campaign. Lieutenant General Michael Flynn, the former Trump campaign and White House adviser, served as an advisory board member to OSY Technologies, an NSO Group offshoot based in Luxembourg, from May 2016 until January 2017. According to financial disclosure forms, Flynn received $40,280 for work completed while he was working for the Trump campaign, and just prior to his ill-fated stint as President Trump’s national security adviser. Flynn also provided consulting work to Francisco Partners, the San Francisco private equity firm that owns NSO Group, for “less than $100,000,” Francisco’s general counsel told the Times.
A year after it bought NSO for around $120 million in 2014, Francisco began exploring a sale of the company. Earlier this year, it entered into discussions about selling 40 percent of NSO Group for $400 million to Blackstone Group, the New York-based private equity firm, a deal that would have valued the company at about $1 billion. The sale was scuttled in August after human rights groups, including Citizen Lab, protested.
Then, this month, Lavie emerged at a cyber conference to announce he was launching a new startup next year, Orchestra, dedicated to cyberdefense.
“I think even from a business perspective, there is clearly risk in this space,” says Scott-Railton, “and we find it very troubling, and we think investors would be concerned too.”
How They Found It
When Mansoor received that text message last August, Citizen Lab investigator Bill Marczak had already been investigating a number of suspicious servers that, it would turn out, were part of the Pegasus’s command and control infrastructure. As he and Scott-Railton revealed in a report that month, “The Million Dollar Dissident,” infiltration attempts with Pegasus begin with a link sent to a target, in the form of a tweet, an innocuous email, or a taunting text message. Once opened in the phone’s web browser, the link connects to one of those servers, where software determines the type of device and installs a remote exploit for the specific operating system.
Not long after that report, a group of researchers in Mexico contacted Citizen Lab, through Amnesty and the human-rights group Access Now, to share suspicious text messages they had collected.
[Photo: Citizen Lab]
“The initial scan that Bill had done left a list of servers that were also part of the NSO exploit infrastructure, so they were spotted to a fingerprint that matched that infrastructure,” says Scott-Railton. “And so we began to look around for other instances of this, and found evidence that something had been happening in Mexico.”
From there, the researchers—from digital rights outfits R3D, Social Tic, and Article 19—would help Citizen Lab determine that over 20 individuals had been improperly and “abusively targeted” with NSO’s spyware. While Mexico, like many other countries, requires individual judicial approval for use of such surveillance, several former Mexican intelligence officials told the Times that it was highly unlikely that the government received such approval for the hacks.
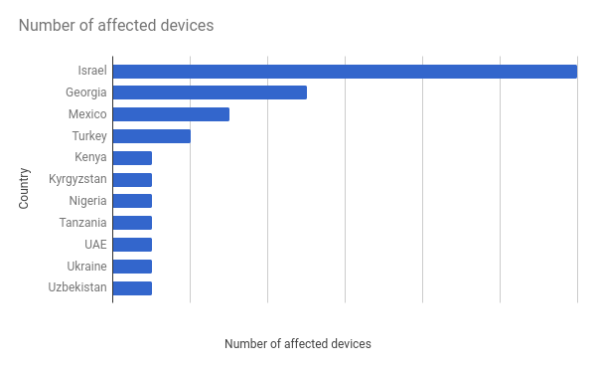
In April, Google said it had found Android versions of Pegasus, called Chrysaor, on “less than three dozen” devices in a wide range of countries, including Mexico, Georgia, Turkey, Kenya, and Ukraine, and Tanzania. One feature of the spyware, “RoomTap,” answers a phone silently, says Google, “and stays connected in the background, allowing the caller to hear conversations within the range of the phone’s microphone.”
Like Pegasus, Chrysaor was “one of the most sophisticated and targeted mobile attacks we’ve seen in the wild,” said Mike Murray, vice president of security intelligence at Lookout, which helped Google discover the spyware.
Apple and Google issued security patches to address the zero-day vulnerabilities NSO had exploited, but given the open-source nature of Android, many of those devices have not received recent security updates. Since Pegasus was first deployed, at least three years ago, security researchers says it’s likely that NSO and other cyberarms makers have developed even more sophisticated techniques.
The Panamanian government has also been caught using Pegasus to hack citizens’ smartphones, alongside a similar weapon by the Italian company Hacking Team called RCS. In 2015, the government of Panama opened an investigation into its former president, Ricardo Martinelli, for running a personal NSO deployment out of a secret office, from which he spied on a number of opponents, including Americans. After receiving a daily briefing with all the doings of his political enemies, Martinelli would even sometimes order subordinates to upload the most salacious material to YouTube.
“Now, that’s already a very problematic track record,” says Scott-Railton. “And NSO is not the first company to sell this stuff and then have it abused.”
Companies like NSO are seeing swelling markets for cyberweapons. Globally, according to the latest forecast from Gartner, spending on information security products and services, including both offensive and defensive measures, will reach $86.4 billion this year, an increase of 7% over 2016; by next year, the number is expected to reach $93 billion.
Big Blackstone Deal Scuttled
In June, after reports emerged this year that Blackstone Group was in negotiations with Francisco Partners to buy part of NSO Group for $400 million, Access Now launched a petition to put pressure on the private equity firm to drop its plans. In its own letter, Citizen Lab told Blackstone that NSO was unable to prevent customers or others from misusing its spying tool, and drew the firm’s attention to over 20 publicly documented cases of reckless misuse of its spyware.
“We would expect such a track record to trigger exceptional due diligence by an American company, and we asked Blackstone if they had done so,” says Scott-Railton. “We also asked what oversight Blackstone proposed to implement to prevent future misuse, if the purchase had gone through.”

[Photo: Citizen Lab]
In August, Reuters reported that Blackstone had pulled out of the deal. The investment firm didn’t comment on the letter or the reasons for its decision not to invest in NSO. But when asked by a reporter for Israel’s Haaretz last month if NSO would have still sold its technology to Mexico in retrospect, one unnamed executive affiliated with the company was emphatic: “No,” they said.
“This research is a reality check to the NSO customers, the same way the reality check happened for Hacking Team and Gamma Group’s customers, which is that it’s not as untraceable as the marketing materials propose,” says Scott-Railton. “And we can say that the NSO saga generally highlights the business, ethical, and human rights risks that come from investing in commercial spyware like NSO.”
Under Israel’s export laws, deals by companies like NSO are supervised by SIBAT, a regulatory body charged with both promoting and reviewing all weapons exports. NSO also has an “ethics committee” that reviews every deal before it is carried out, according to one company official who spoke with The Marker.
But Scott-Railton says companies like NSO must institute more thorough vetting processes. Given the history of abuse of spyware like Gamma Group’s Finfisher and Hacking Team’s exploits, any cyberweapons maker must be aware of the potential for abuse, he says, arguing that each of the three cases he’s investigated—Mexico, United Arab Emirates, and Panama—demonstrates a failure of due diligence.
[Image: Censoo]
“What my colleagues and I say informally is, there is the principle of misuse, where it’s only a matter of time if you sell this kind of software to a government that doesn’t have very rigorous rules in place before it gets misused,” adds Scott-Railton. “It’s clear that the industry that sells the commercial spyware to governments is not wired to take that very basic fact into account and mitigate it.”
And if companies like NSO become aware of abuse, he adds, they should also take affirmative steps to stop it. Otherwise, he believes, it’s a foregone conclusion that exploits like Pegasus will be misused.
Doubts Surround Mexico’s Investigation
It’s still not clear who exactly in Mexico was using Pegasus. But the government’s inquiry has been hobbled by an apparent unwillingness to audit the cellular modem deployed in the attacks, and by what forensic experts have called an unneeded request: Investigators have told victims that they must turn over their phones so the government can verify that the spyware is indeed on their devices.
“There are a lot of ways to conduct this investigation,” says Scott-Railton, “but it seems that starting by asking for cell phones is asking victims for what they may be most uncomfortable giving up, especially given that in many of their minds, it was the same attorney general’s office that may have targeted them.”
All that Mexican investigators would need, he says, are phone and internet service provider records that they are legally mandated to store, and which are legally admissible in court. One could see, for instance, the date the messages were sent, then ask ISPs for the actual messages’ content. In the Panamanian case, Scott-Railton noted, investigators did not need to inspect victims’ phones.
“Infection attempts with this are, according to our Mexican colleagues, illegal in themselves,” he says. “This raises interesting challenges for an investigation, and is why any official investigation should focus on text message records to see if infection attempts were made.”
It’s also not clear what impact the various abuses of NSO software have had on the company’s business. But as the scandal in Mexico was unfolding this summer, cofounder Omri Lavie was preparing the launch of a new startup, Orchestra, dedicated not to attacking devices but protecting them.
“The biggest thing we are focused on is that we believe there is a little too much going on,” he told Reuters at its Cyber Summit in early November. (A startup launched by the NSO founders in 2013, Kaymera, is also focused on cybersecurity.) “The situation [the cybersecurity industry] has right now is that we have a multitude of companies, each of them solving a very small and niche problem for [overwhelmed] security staff.”
Lavie didn’t say if he would discontinue his work for NSO to focus on Orchestra. When asked by Reuters about abuses of NSO software in Mexico and elsewhere, he said, “I think people believe that NSO is a company that does good. [Security experts] understand the value that this company has generated for the world. I am extremely proud of NSO.”
Fast Company , Read Full Story
(23)














