Hot New Cryptocurrency Trend: Mining Malware That Could Fry Your Phone
Like many people, hackers on the message board Hack Forums are trading tips on how to make money with cryptocurrency. But they’re not just looking to buy low and sell high. They’re swapping ways to surreptitiously harness other people’s phones and computers to generate digital coins for themselves.
“Perhaps anyone with a few hacked website panels can inject the simple JavaScript miner into the webpage?” asks one user, called Ungifted, seeking help with code that mines the cryptocurrency monero when users visit a site where it’s deployed.
Another forum member, using the name Broke Musician, suggests injecting the program into third-party websites, or sending out links to sites with the mining code through social media and spam.
Hack Forums isn’t the most elite gathering of cybercriminals. Many of its members seem to be relative novices, and it’s likely some post about hacking techniques they’ve never actually attempted. But experts say that with the recent bull market in cryptocurrencies, even sophisticated hacking groups are getting into clandestine mining, sometimes running such operations alongside more traditional cybercrime like data theft and denial of service attacks. Recent reports have also implicated North Korean government hackers in efforts to hijack CPUs to mine cryptocurrency.
“We definitely feel like these guys are a little more sophisticated than your average bot herder,” says Sara Boddy, principal threat researcher at F5 Networks, a Seattle security firm. Last month, it reported a “sophisticated multi-stage attack” hijacking networks of computers to mine cryptocurrencies. Those attackers used vulnerabilities in common server software, coupled with Windows exploits leaked from the National Security Agency, to penetrate victims’ systems and migrate through their networks. Another piece of malware F5 reported this week targets Linux systems, logging into them by guessing credentials and then runs a monero-mining script.
It’s hard to know exactly how much these recent cryptojacking attacks have earned in total, but three addresses linked to both of the malware variants appeared to receive a total of $68,500 in the cryptocurrency monero. The three-year-old currency has become the instrument of choice for illicit mining operations. It’s designed with privacy and anonymity in mind—transaction party IDs and even transactions amounts are deliberately obfuscated in its public ledger—so it’s relatively hard to trace ill-gotten gains across the ledger, or blockchain, that records transactions in the currency.
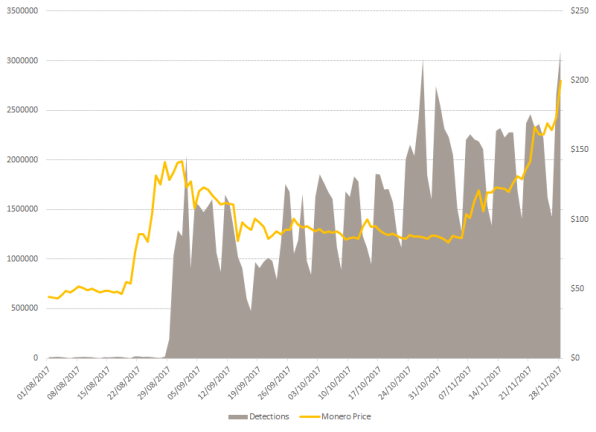
Perhaps equally importantly, monero is built around algorithms that let people with ordinary computers take part in the typical mining process, whereby users are paid to log transactions to that digital ledger. Other currencies, including bitcoin, can effectively only be mined with specialized, high-end hardware.
The currency, which now boasts a market cap of $6.3 billion, has legitimate uses as well. Last month monero core developer Riccardo “fluffypony” Spagni announced that it can be used to purchase music and merchandise from well-known recording artists including Weezer and Mariah Carey. And some cryptocurrency fans appreciate its emphasis on privacy and a democratic approach to mining.
But in the past year, monero-mining malware has been spotted on a wide range of websites, mining the currency as people streamed videos from Showtime and Ultimate Fighting Championship or merely browsed the web on compromised Wi-Fi networks at Starbucks cafes. Hackers linked to the North Korean government have even been accused of spreading monero malware, presumably to raise money for the perennially cash-strapped state. (One attack on a South Korean server reportedly mined about 70 monero coins—worth about $27,000.) Some browser extensions have been caught mining the currency while users do other things, and monero-mining malware has recently been spotted propagating through links on Facebook Messenger. Wandera, a mobile security firm, reported last month that the number of mobile devices it spotted connecting to malware mining websites and apps rose 287% between October and November.
Hi @Starbucks @StarbucksAr did you know that your in-store wifi provider in Buenos Aires forces a 10 second delay when you first connect to the wifi so it can mine bitcoin using a customer’s laptop? Feels a little off-brand.. cc @GMFlickinger pic.twitter.com/VkVVdSfUtT
— Noah Dinkin (@imnoah) December 2, 2017
“If you remember the IoT botnets, Mirai in the past, we’ve actually seen one variant this year which was mining monero coins on routers and hard disk recorders as well,” says Candid Wueest, principal threat researcher at Symantec and contributing author on a report the security company released on cryptojacking last month.
Meanwhile, mining malware is also finding its way into the ad networks that are common to many website. One JavaScript-enabled ad discovered by adtech firm Spotad was designed to trick users into clicking on a pop-up to start mining monero. According to Spotad, the agency responsible for the ad was unaware of the malicious code.
Stealing Pennies And Killing Batteries
Websites surreptitiously mining monero might only make a few cents for every hour a user spends on an infected page, according to the Symantec report. But with enough traffic, those pennies start to add up.
For unsuspecting computer owners, the electricity costs aren’t that significant: perhaps only a couple of dollars a year, Wueest estimates. “The main thing you will notice as a user is your CPU is running at 80% or 100%, which makes your whole computer quite slow,” he says.
And on smartphones, unwanted mining can tax CPUs and run down batteries, shortening device lifetimes, and even causing physical damage.
Kaspersky Lab, the Russian security firm, recently reported detecting mobile malware that mines monero, bombards users with unwanted ads, and can even be used to launch denial of service attacks. “We’ve never seen such a ‘jack of all trades’ before,” researchers wrote in a blog post.

After two days of testing, they wrote, an infected device showed physical trauma: the overworked battery swelled up, damaging the phone’s outer shell.
Like with other types of unwanted software, security experts say users looking to avoid parasitic mining should only install apps from trusted sources, keep systems patched, and run anti-malware tools to purge their systems of suspicious code. For web-based mining systems, adblocking software can also help filter out the JavaScript code that enables unwanted cryptocurrency number-crunching. And hardware or software firewalls can disrupt connections between mining tools and their command servers.
“Without this connection, it cannot get the data it needs to generate hashes, rendering it useless,” according to the Symantec report.
Legit Uses
Makers of some monero-mining software argue that in-browser mining can have a legitimate use, letting people knowingly trade computer power for access to articles, videos, or premium app features, at a time when websites are looking beyond advertising as a revenue stream.
“I don’t agree with anyone’s computer being abused without their knowledge,” says Spagni, the monero core developer. “Yet the technology that is being abused presents an entirely new way of monetizing a service on the internet.” He argues that this could enable a “free” version of Netflix or provide a new funding stream for journalism.
Coinhive, one of the most well-known web miners, evolved from an experimental feature on the German forum site Pr0gramm, Coinhive’s developers write in an email to Fast Company. Pr0gramm users liked being able to trade mining time for premium accounts, so the developers built Coinhive as a tool usable on other sites.
“For example, a few porn sites use Coinhive and let user’s disable advertisements or offer premium accounts,” they write. “Porn ads are typically very intrusive and not that lucrative, so it’s a welcome alternative for users and site owners.”
Coinhive even offers a mining-based captcha alternative, aimed at making it less feasible for spammers to perform certain actions on a website, and a version of the software called AuthedMine requires users to explicitly opt in before mining begins.
“We don’t think it’s a good idea to let the miner run without consent of the user or without at least telling them what’s going on,” Coinhive’s developers write. “Again, if users can get something in return, they’re happy to run the miner for long periods. So it’s only in the site owner’s interests to come up with good ways to integrate the miner openly.”
It’s potentially in the developers’ interests as well—they’ve asked antivirus software makers not to block AuthedMine, since they say it can only be run with explicit permission.
Creators of other mining tools make similar statements about user consent, perhaps with varying degrees of sincerity.
A tool called Monero Silent Miner, available for $14, mines in the background on Windows PCs. It doesn’t launch a visible window that users can detect, keeps the devices from going to sleep, and is able to “bypass firewalls,” according to its website. A Windows registry setting ensures the miner starts working when the computer is restarted, and if that setting is removed, it will automatically restore itself.
But in an email to Fast Company, its developer, who declined to give any identifying information, wrote that it’s only intended for “legitimate users.” Those could include people who own multiple computers and want to use them to mine monero “transparently for the end user of the PC.”
The developer reports selling about 700 copies of the software so far.
Fast Company , Read Full Story
(39)



