Profiling Hackers: Defining the Good, Bad, and Ugly Personas
Profiling Hackers: Defining the Good, Bad, and Ugly Personas

It’s easy to put all hackers in one box. In reality, there are a few types of hackers — some good, some bad. And, yes, some ugly in terms of what they do. While you are used to hearing about those hackers that steal your personal and payment data, there are ethical hackers out there working to protect that very same data.
To better understand what’s going on with data, it’s good to know what each type of hacker looks like and what they do.
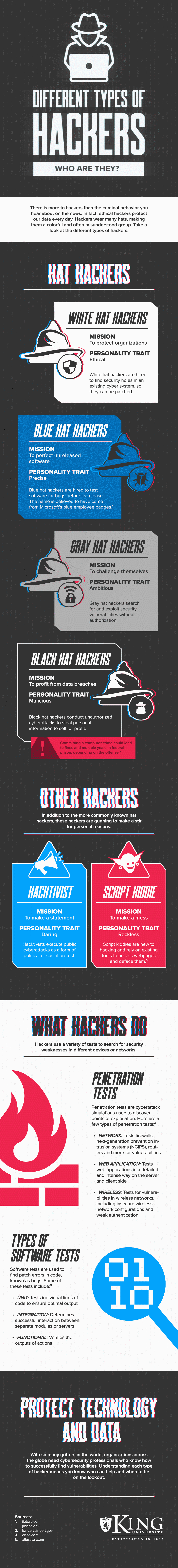
Hat Hackers
Let’s start with the good guys — the white hat hackers. Hired to protect an organization, these ethical hackers look for breaches and potential vulnerabilities in an organization’s systems where a hacker with bad intentions can get to data.
Blue hackers are also on the side of good. They are hired to test software that’s been developed but not released to the public. These hackers are looking for bugs that can be addressed prior to launch so that those bugs don’t create vulnerabilities for other hackers to later exploit.
Gray hat hackers are just as they sound — they exist in that gray area between good an bad. They are looking to challenge their own hacking abilities but don’t necessarily want to take anything from those they are able to hack. They seek out vulnerabilities without specifically being asked by companies like white and blue hackers do.
Then there are black hat hackers, which are just like they sound. With nothing but malicious results in mind, these hackers are out to profit from their hacking. They steal other people’s data to make money by selling it or using it themselves.
Other Types of Hackers
Beyond the hat hackers, there are other types of hackers out there with their own objectives.
First, there’s the hacktivist. To make a statement, they thrive on daring behavior that gets them noticed. They use public cyberattacks as a platform for social or political activism.
Next, there are script kiddies that are just looking to create mayhem and confusion. They are relatively new to hacking so do little than use existing hacking methods to deface websites. Think of them as graffiti artists for the cyber environment.
Hacker Methods
There are many methods hackers use to test and identify vulnerabilities that let them get to the desired data. The first is a penetration test, which stimulates a cyber attack to see what might happen. A network penetration test focuses on potential vulnerabilities in firewalls, routers, and any other point in a network. Web application penetration tests pursue client- and server-side aspects of web applications. Wireless networks also have their own penetration test.
Other methods include software tests that identify bugs and other vulnerabilities in software programs and apps. There are unit, integration, and functional software tests that hackers use.
Stay Vigilant
With so much at stake with the amount of personal data that is now shared and the accountability that falls on companies that accept this data, this is the time to stay vigilant and understand the threat is out there as well as the methods these hackers use to get what they want.
To learn more about hackers, check out this infographic from King University Online.
The post Profiling Hackers: Defining the Good, Bad, and Ugly Personas appeared first on ReadWrite.
(6)