Study finds five major US carriers vulnerable to SIM-swapping tactics
A Princeton study (PDF) has discovered that five US prepaid carriers use authentication techniques that are vulnerable to SIM-swapping tactics. The researchers signed up for 10 prepaid accounts each on AT&T, T-Mobile, Tracfone, US Mobile and Verizon Wireless for a total of 50. They found that they only needed to successfully answer one thing to verify their identity and get the companies to switch their service to a SIM card they already have. It didn’t even matter if they got the other authentication challenges wrong.
Verizon owns Engadget’s parent company, Verizon Media. Rest assured, Verizon has no control over our coverage. Engadget remains editorially independent.
That kind of SIM-swapping technique could be used by attackers to gain control of a victim’s phone number. They can then use that number to reset the victim’s passwords and access, say, their emails and bank accounts.
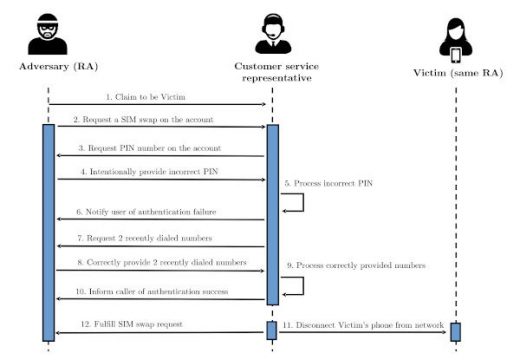
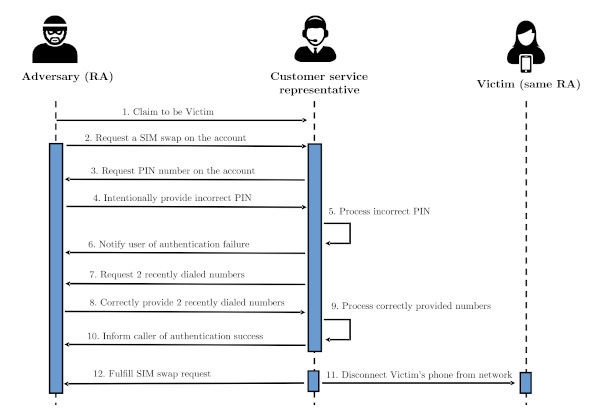
To test the carriers’ security measures, they called the companies to request for a SIM swap and intentionally provided the wrong PIN number to force the customer service rep to try another authentication method. When asked for the account holder’s date of birth or billing ZIP code, they’d say that they must’ve made a mistake upon signup and provided the wrong information.
The customer service rep would then have to move to a third type of authentication method, which is asking the caller for their two most recently made calls. It was through this method that the researchers were successfully able to complete the SIM swaps. And that’s alarming, since attackers can easily trick victims into calling random phone numbers.
In addition, the researchers examined 140 popular online sites and services that use phone authentication to see what attackers can do with the numbers they hijack. They were easily able to reset passwords on 17 of those services using only the hijacked SIMs, since they weren’t asked additional authentication questions.
The Princeton researchers provided a copy of their findings to the carriers last year, and T-Mobile notified them this month that it doesn’t use call logs as a form of authentication anymore. We’ve reached out to the other four carriers for a statement.
Update 1/13/2019 2:45 AM ET: A T-Mobile spokesperson has given Engadget the following written statement: “We take the protection of our customers’ accounts very seriously. We have implemented many safeguards and will make continuous improvements as we need to respond to new risks. Most recently, this included changing our authentication processes on T-Mobile prepaid accounts to prevent the use of call log information for authentication.”
Verizon SVP Nick Ludlum has also responded to Engadget with the following written statement: “Wireless operators are committed to protecting consumers and combating SIM swap attacks. We continuously review and update our cybersecurity practices and develop new consumer protections. We all have a role to play in fighting fraud and we encourage consumers to use the many tools highlighted in this study to safeguard their personal information.”
Update, 1/13/2019 11:00 AM ET: US Mobile has issued a statement, part of which you can read below:
“US Mobile has historically received less than 1% of its SIM swapping requests over the phone. Furthermore, SIM swapping over the phone to our CSR’s is no longer possible. They must be initiated from authenticated status while signed in to our app or dashboard. Considering that the study failed to take into consideration that US Mobile was fully digital, it does not reflect how the majority of SIM swapping happens at US Mobile.”
(68)