Up to 90 million Facebook Accounts Hacked. What Do Businesses Need to Know?
— September 29, 2018

Simon / Pixabay
The New York Times broke a story on Friday night reporting that up to 90 million Facebook accounts were breached by hackers.
50 million accounts were potentially directly affected, but Facebook has logged out an extra 40 million accounts as a security measure.
This is yet another challenge on top of Facebook’s difficult year, with critiques about how they handle fake news, can be used to influence elections, anti-trust/competition legislation, and their use, collection and storage of user data.
The bug was introduced as part of changes to improve privacy controls (ironic) and another feature intended to make it easy to upload birthday videos. It meant that potentially anyone could take over any Facebook account and have full access – but not just Facebook, also any third party platforms connected to the account (whether Spotify or … Instagram).
Facebook’s team reported that Mark Zuckerberg and Sheryl Sandberg’s accounts were included in those potentially accessed. The hackers reportedly tried to export all the information Facebook held about these accounts.
There’s a good Tweet thread from reporter Mike Isaac that mentions some of the responses from US senators and a FTC commissioner, but I’m sure we will continue to see more calls to arms in the coming days.
It’s still very early days, and maybe it’s all a storm in a teacup, but what does this mean for businesses?
Facebook logins reset = reset API access keys
For social media managers using a swarm of services for scheduling, reporting, advertising and more – when your Facebook login gets reset, you will often find that Facebook will invalidate the API access keys any services hold.
This is a good security feature (as if someone got access to the account, they could then have access to these third party services) – but it can be an absolute nightmare to reconnect a whole lot of services to Facebook again (note: Schedugram isn’t affected by this).
When you see notifications about needing to re-add Facebook access to platforms, please be patient: it’s not the fault of the software tools, it’s just what happens when this kind of breach occurs.
Schedule a bit of time though to double check that your main services are all running OK, lest you discover when you go to compile that all-important end of month report that you have no data!
Hacked Facebook = Hacked Instagram
Increasingly users are connecting their Facebook accounts to Instagram – for businesses, that’s usually when you change your Instagram account from a personal profile to a business profile.
The benefits are numerous (like having insights access, being able to run Instagram ads etc), but the downside is that the Facebook account(s) of anyone who has access to that business profile are another avenue that someone can nefariously access your Instagram account.
A hacker could reasonably breach one of these Facebook profiles, log into Instagram, then change the email address on file and password to the account – and then disconnect the Facebook business profile. Voila, you’ve now lost access to your Instagram account.
The episode underscores the principle that every account you have is a potentially weak link that can crack open almost any door.
Email is clearly one of the biggest centralized services businesses have (as you can use the forgot password function to get access to anything from social media to banking), but given how prolific “Login with Facebook” has become, access to Facebook is starting to look similar.
What should you do to protect yourself?
One of the most common mechanisms for people to “hack accounts” is poor password practice (not the case here with Facebook – it was a bug, but wanted to use the opportunity to highlight some of the simple rules about security).
Don’t reuse passwords across services.
With the frequency of breaches occurring for platforms from forums to LinkedIn, that password you’ve been using for 10 years is undoubtedly associated with your email somewhere.
Use complex and non-guessable passwords.
“Password123” is definitely still seen in the wild. Nike using a password like “n1ke2018” or even “Nike2018” would be insanely stupid.
Use complex passwords that are not easily guessed, and don’t form a regular pattern. A password manager helps a lot in keeping track of all these (keep in mind you need at least one complex password that you remember though, for the password manager itself!), and most will also generate new passwords for you.
Don’t share passwords among team members (if at all possible).
Shared passwords commonly need to be simple enough for people to remember (at the very least, share using a complex password and a password manager!).
One of the main reasons that we have unlimited free collaborator users for every Schedugram account is that the security impact of shared passwords (common in brands and agencies, particularly if their software charges per-user) is huge.
We don’t think that someone’s pricing model should be the reason that you leave yourself open to that.
Consider using two-factor authentication
Two-factor authentication isn’t entirely the holy grail (particularly when it’s SMS based two-factor authentication…), but it can help and certainly make it harder for automated hacking attempts.
However, it can also make it a lot harder to get your work done when you are collaborating with other users (note: you can add two-factor login to your Schedugram login, but we only support two factor Instagram login with enterprise customers at present).
We also see a lot of difficulty when people get new phones or lose one, and resetting that second factor can be a nightmare if you have to do it across a lot of services (having experienced it myself…).
Checking if you are affected by a Security breach
Facebook is informing all affected users using a notification at the top of the service when they next login.
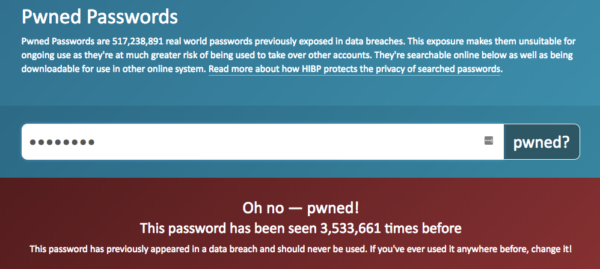
Australian security researcher Troy Hunt runs Have I Been Pwned (read the FAQ), a service that collects all of the security breaches and password lists for sale in the wild (note: this Facebook breach isn’t included – it wasn’t passwords that were breached).
The service is great to see if your email is associated with any breaches, and domain administrators can sign up to get alerts if any email appears in a breach with their domain name.
You can also check if the password you are using is seen in other breaches (click ‘password’ in the header). Here’s “password”:
Digital & Social Articles on Business 2 Community
(44)